Stop hiring impostors
Hackers try to pose as the perfect candidate.
imper.ai detects them at the first point of contact, so you know you’re hiring and onboarding the right person.


In the news: North Korean hacker infiltrates KnowBe4
In 2024, KnowBe4 hired a ‘software engineer’ for its internal IT AI team. The candidate made it through video interviews and background checks, so the company onboarded them.
Read full articleHackers use voice cloning, deepfakes or AI-generated profiles to pose as real candidates.
Bring them in, and you’ll never know what goes out.
imper.ai checks their digital identity markers at every stage – from first application to their final video interview.
Verify phone and
video interviews
Hackers clone real candidates’ voices and faces during remote interviews – impersonations are getting more convincing.
imper.ai ignores the content and checks their network, device and digital identity markers for red flags instead.
Detect synthetic
& high-risk applicants
Nation-state and criminal actors use stolen data and AI-generated profiles to pose as ideal candidates — aiming to steal data or move illicit funds.
imper.ai analyzes security signals to detect impersonation and stop fake applicants before they reach your hiring team.
You look for candidates.
imper.ai looks for hackers.
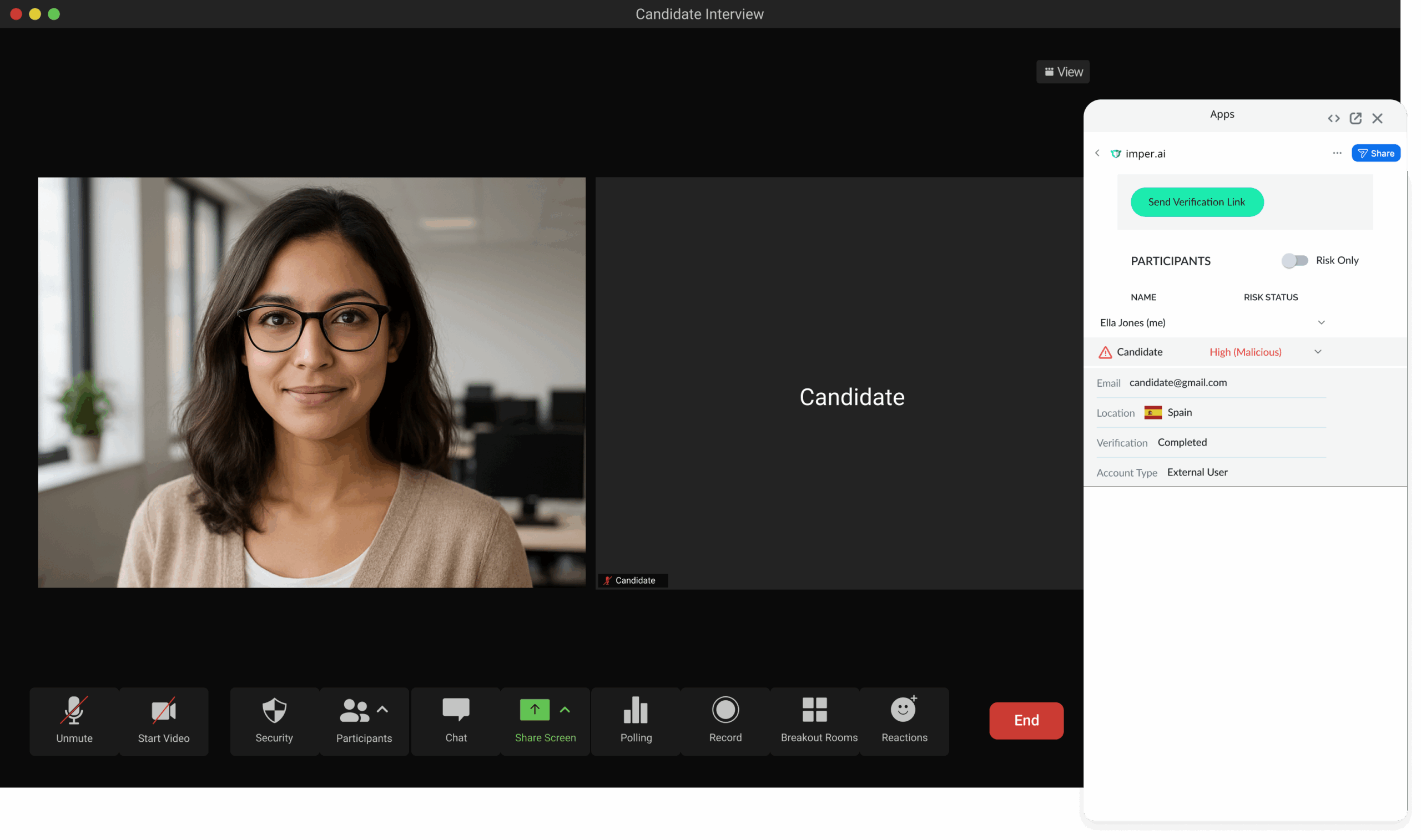
Interview validation initiated
Use existing hiring workflows. The platform integrates directly with your applicant tracking system to validate candidate identities before interviews even begin – no new steps for your recruiters.
Detect fraudulent
candidates instantly
imper.ai analyzes digital fingerprints – from device, network, and digital identity signals—and correlates them with ATS data to generate a real-time risk score. Suspicious profiles are flagged instantly, stopping impersonators before they enter your hiring funnel.
Hire with
confidence
Once verified, recruiters and hiring managers can proceed knowing every hire is genuine and secure.
Multi-layered impersonation detection and prevention
Hackers can steal candidates’ faces, voices, job histories, and
qualifications more convincingly than ever.
So imper.ai ignores the contents of their messages, applications, videos
and calls – and looks at the forensic markers including network, device and
digital identity that hackers can’t hide.
