Stop scams involving your
customers and partners
Verify every customer, partner and payment request at first contact in real time – blocking impersonators before they exploit your trust.
Try imper.ai now
Jaguar Land Rover Supply Chain is hacked
JLR experienced a significant supply chain attack on Sept 1, 2025; losses are estimated to total ~$2 billion. Hackers succeeded in stealing customer data and causing a complete shutdown of JLR’s production, IT and retail systems.
Read full articleReal vendors get through.
Hackers get left on the doorstep.
Bad actors impersonate your trusted vendors and customers—hijacking accounts, mimicking voices, and cloning brands to steal payments or deploy ransomware.
imper.ai verifies who’s really behind every message, call, and transaction, using security signals across devices, networks, and digital identity, so only legitimate third parties ever get through.
Prevent invoice fraud
& payment diversion
Social engineers impersonate legitimate vendors to redirect payments or update banking details.
imper.ai combines device fingerprinting, network intelligence, and digital identity telemetry to verify every request in real time — detecting impostors and signals that indicate someone is posing as a vendor.
Authenticate vendors and customers
Impostors clone vendor domains, spoof customer identities, and hijack accounts to gain access.
imper.ai analyzes security signals to detect impersonation and stop hackers from gaining access to sensitive data so your teams can trust every connection without slowing down business.
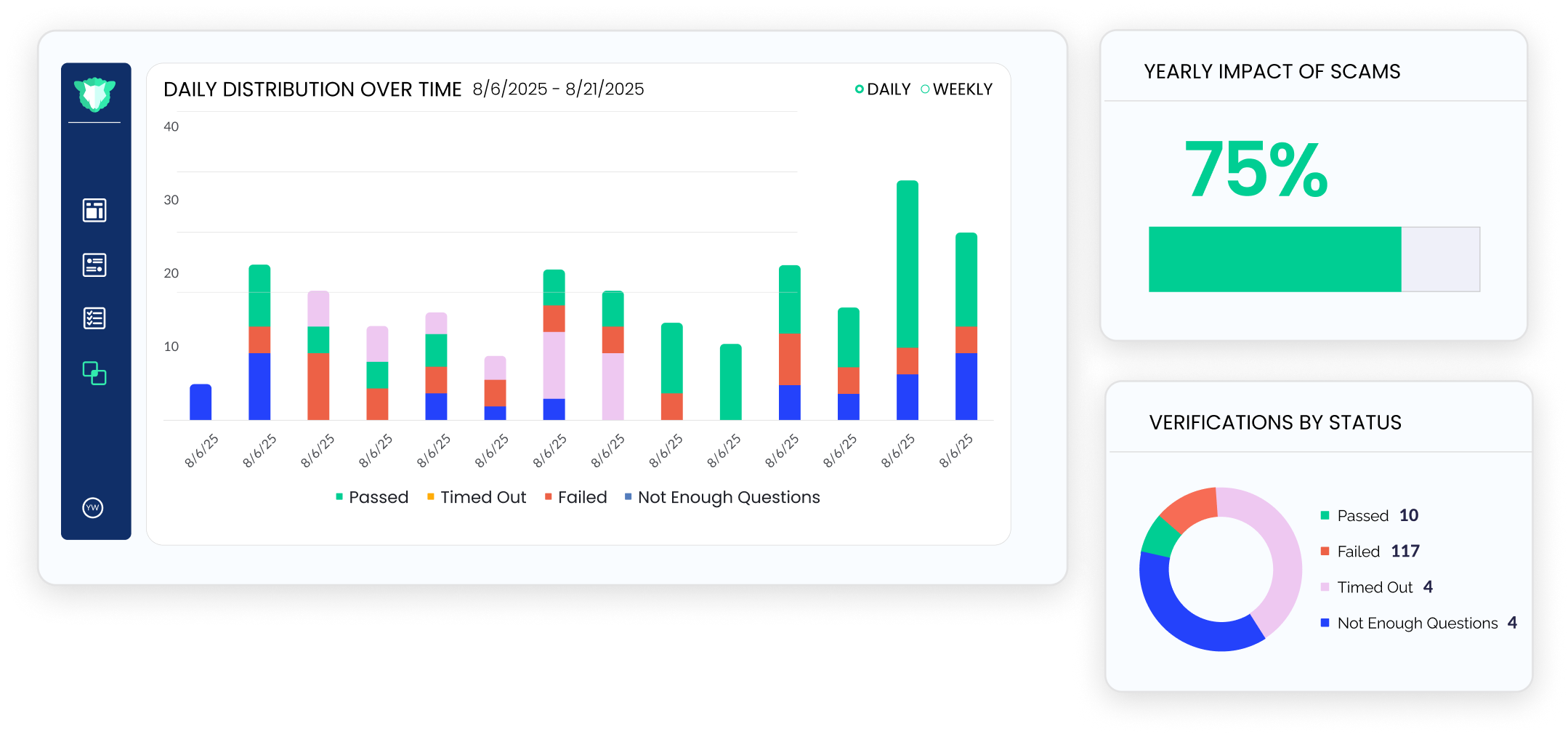
Validation initiated
Every new or modified vendor or customer interaction is sent the validation link.
Risk score
detected
imper.ai analyzes digital fingerprints — from device, network, and identity signals — in seconds to confirm whether a request comes from a legitimate contact or an impersonator. It then generates a real-time risk score, flagging suspicious signals instantly to stop impostors before any access or payment occurs.
Trust established
Once verified, the interaction is cleared for normal business flow, whether it’s a payment, contract update, or data exchange.
Multi-layered impersonation detection and prevention
imper.ai analyzes the forensic markers hackers and social engineers can’t hide — from device fingerprints and network intelligence to digital identity.
By correlating hundreds of real-time security signals, it exposes hidden impersonation attempts before fraud or data loss occurs.
A global insurer was threatened by a wave of attacks designed to steal data and trigger fraudulent payouts – until they pursued a solution to help detect and assure the identities of customers, colleagues and vendors in real time.
Read the full story
